Attackers use dynamic code loading to bypass Google Play store's
Por um escritor misterioso
Last updated 05 julho 2024

Threat actors rely on the 'versioning' technique to evade malware detections of malicious code uploaded to the Google Play Store

One Click Hijack: Vulnerability in TikTok Android App?
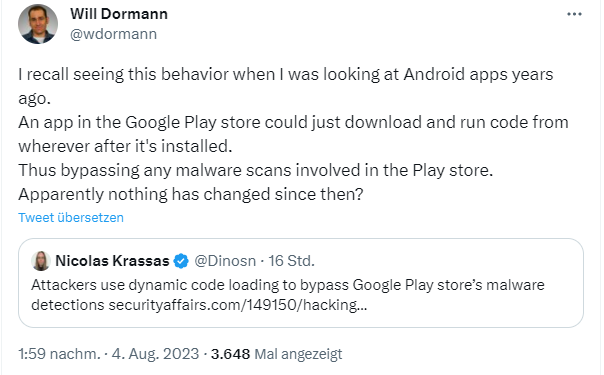
Bypass malware detection in Google Play Store with Dynamic Code

Google Play Store, Breaking Cybersecurity News

Cyberattack Disrupts Hospital Computer Systems Across US, Oregon

The many lives of BlackCat ransomware

Cyble — Hydra Android Malware Distributed Via Play Store
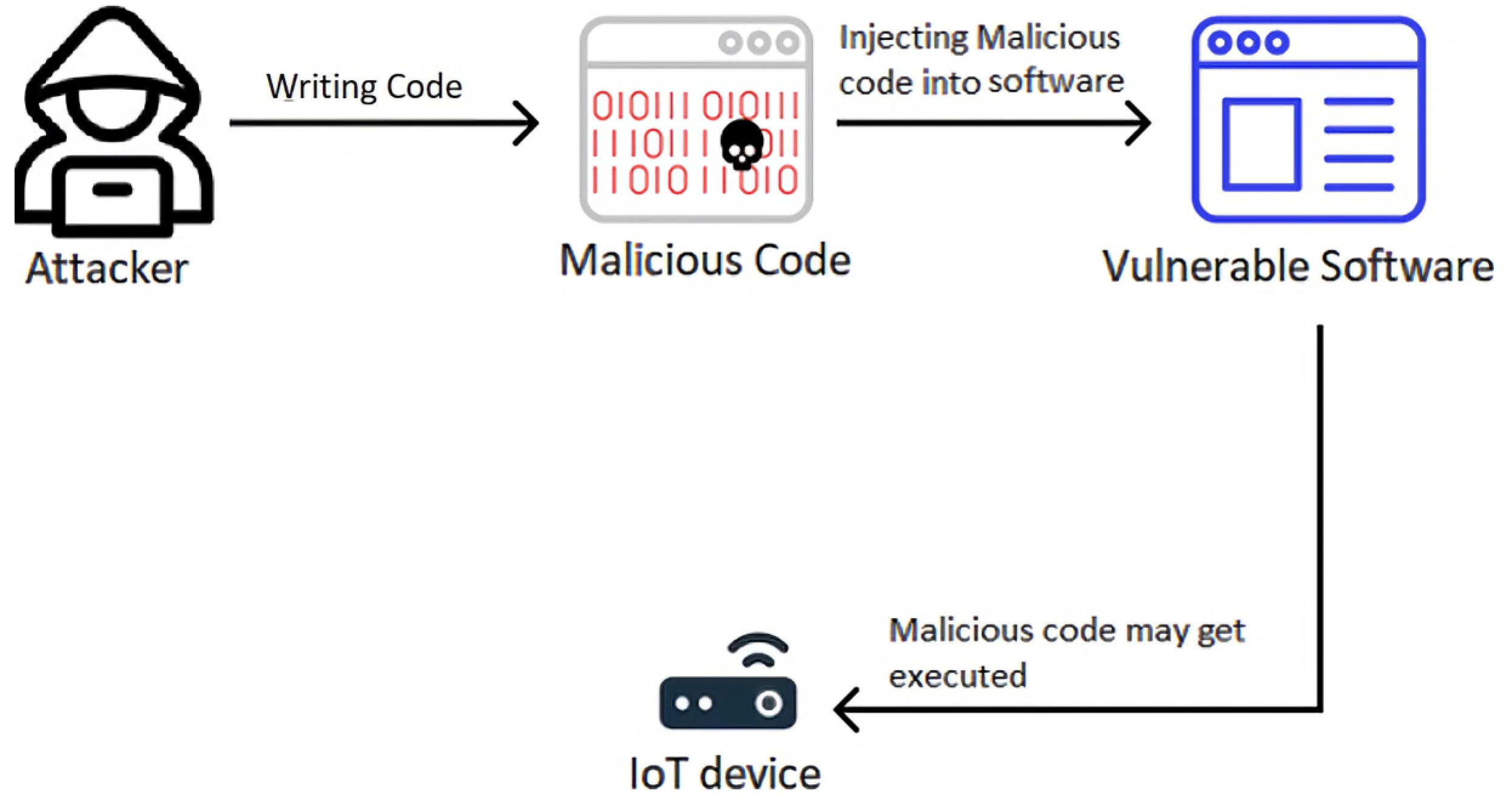
Sensors, Free Full-Text

How to Code Sign Secured Android App with SHA Fingerprint Google
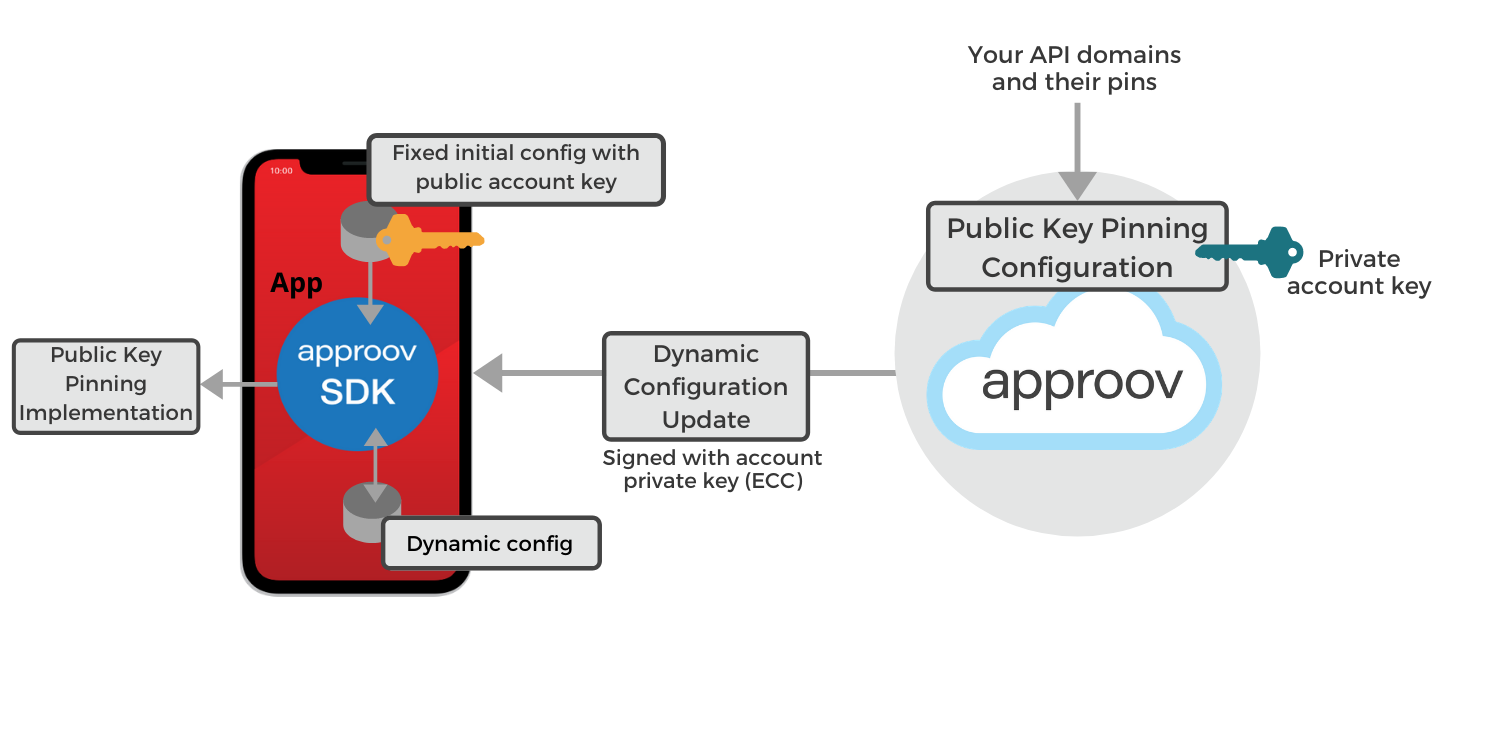
How to Protect Against Certificate Pinning Bypassing

HeadCrab: A Novel State-of-the-Art Redis Malware in a Global Campaign

From GitHub to Account Takeover: Misconfigured Actions Place GCP

Android Applications Pentesting - HackTricks
Recomendado para você
-
 All Roblox Zo Samurai codes for free Shards & Spins in December05 julho 2024
All Roblox Zo Samurai codes for free Shards & Spins in December05 julho 2024 -
 Evade Codes 2023 Free Bots, tokens, points, by Gamejul05 julho 2024
Evade Codes 2023 Free Bots, tokens, points, by Gamejul05 julho 2024 -
 Hexagon Development Community on X: Use code 'luckyday' in Evade for some pin thing. There's also an update out that's kinda cool / X05 julho 2024
Hexagon Development Community on X: Use code 'luckyday' in Evade for some pin thing. There's also an update out that's kinda cool / X05 julho 2024 -
 Evade 🍀 Codes Wiki 2023 - St Patricks Update Codes05 julho 2024
Evade 🍀 Codes Wiki 2023 - St Patricks Update Codes05 julho 2024 -
 read desc) NEW EVADE SECRET CODES! (2023 Celebration unusual showcase) - Roblox Evade05 julho 2024
read desc) NEW EVADE SECRET CODES! (2023 Celebration unusual showcase) - Roblox Evade05 julho 2024 -
 Evade codes December 2023 - PROJAKER05 julho 2024
Evade codes December 2023 - PROJAKER05 julho 2024 -
 Utilizing Morse Code to Evade Signature Based Detection Systems05 julho 2024
Utilizing Morse Code to Evade Signature Based Detection Systems05 julho 2024 -
 Codes Roblox Evolution Evade (août 2021)05 julho 2024
Codes Roblox Evolution Evade (août 2021)05 julho 2024 -
 Roblox Evolution Evade Codes January 2023 in 202305 julho 2024
Roblox Evolution Evade Codes January 2023 in 202305 julho 2024 -
 College Presidents Under Fire After Dodging Questions About05 julho 2024
College Presidents Under Fire After Dodging Questions About05 julho 2024
você pode gostar
-
 YashaHime: Sequência de 'InuYasha' ganha novo trailer e data de05 julho 2024
YashaHime: Sequência de 'InuYasha' ganha novo trailer e data de05 julho 2024 -
Gluten-Free Menu - Photo from IHOP05 julho 2024
-
 Sad Alone Heart Touching Mashup Official Resso album by Bittu Mehta 8 - Listening To All 1 Musics On Resso05 julho 2024
Sad Alone Heart Touching Mashup Official Resso album by Bittu Mehta 8 - Listening To All 1 Musics On Resso05 julho 2024 -
 Jullius Granada - Watch Dogs: Legion05 julho 2024
Jullius Granada - Watch Dogs: Legion05 julho 2024 -
 Roblox Promo Codes November 2023 - Free Robux on X: Exclusive05 julho 2024
Roblox Promo Codes November 2023 - Free Robux on X: Exclusive05 julho 2024 -
 NEW* Reaper 2 Script/Hack GUIs, AutoFarm, Infinite Money05 julho 2024
NEW* Reaper 2 Script/Hack GUIs, AutoFarm, Infinite Money05 julho 2024 -
 remake/edited weirdcore eye les-bian05 julho 2024
remake/edited weirdcore eye les-bian05 julho 2024 -
 Celebrate Earth Day with Minecraft05 julho 2024
Celebrate Earth Day with Minecraft05 julho 2024 -
Cross Check-In APK (Android App) - Free Download05 julho 2024
-
 What's wrong with 2042 : r/Battlefield05 julho 2024
What's wrong with 2042 : r/Battlefield05 julho 2024