To Be (Enumerated) Or Not To Be
Por um escritor misterioso
Last updated 05 julho 2024
Are user enumeration vulnerabilities a real security concern? User enumeration is when an application reveals whether a user exists to other users.

Why the 9th Amendment? – Frank Kuchar, Constitutionalist
Use Enumerated Data in Simulink Models - MATLAB & Simulink
As illustrated for the nearly 3000 enumerated reaction pathways to

Uintah Shivwits - Kansas City Star Archive
What Enumerated and Unenumerated Rights Does an American Have

James Madison quote: In the first place, it is to be remembered
Key Facts

What is an Enumeration Attack? How they Work + Prevention Tips

23 Implied Powers Examples (US Government) (2023)
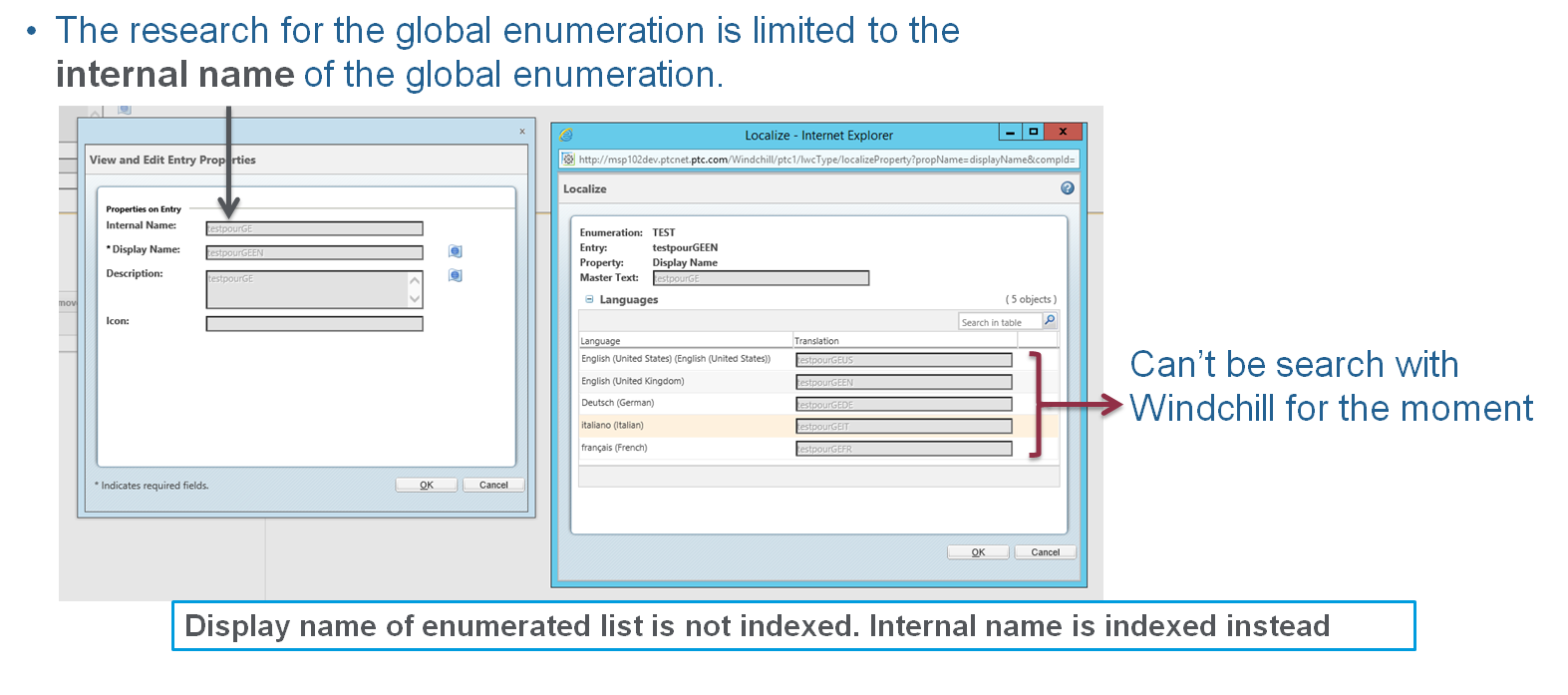
Extend SolR capabilities to Global Enumeration Dis - PTC Community

Enumerations in C
Enumeration - Definition and Examples - Poem Analysis

Python enumerate Explained with Examples - Spark By {Examples}

What Is Enumeration in Ethical Hacking? [Updated 2023]
Recomendado para você
-
 Log into Facebook05 julho 2024
Log into Facebook05 julho 2024 -
 How to identify the owner of a phone number you don't recognize05 julho 2024
How to identify the owner of a phone number you don't recognize05 julho 2024 -
 Ionic Facebook Login05 julho 2024
Ionic Facebook Login05 julho 2024 -
 Facebook 2FA is stuck in a loop and I have tried everything I can05 julho 2024
Facebook 2FA is stuck in a loop and I have tried everything I can05 julho 2024 -
 Facebook Warning For Koobface Virus - How to Restore your Facebook05 julho 2024
Facebook Warning For Koobface Virus - How to Restore your Facebook05 julho 2024 -
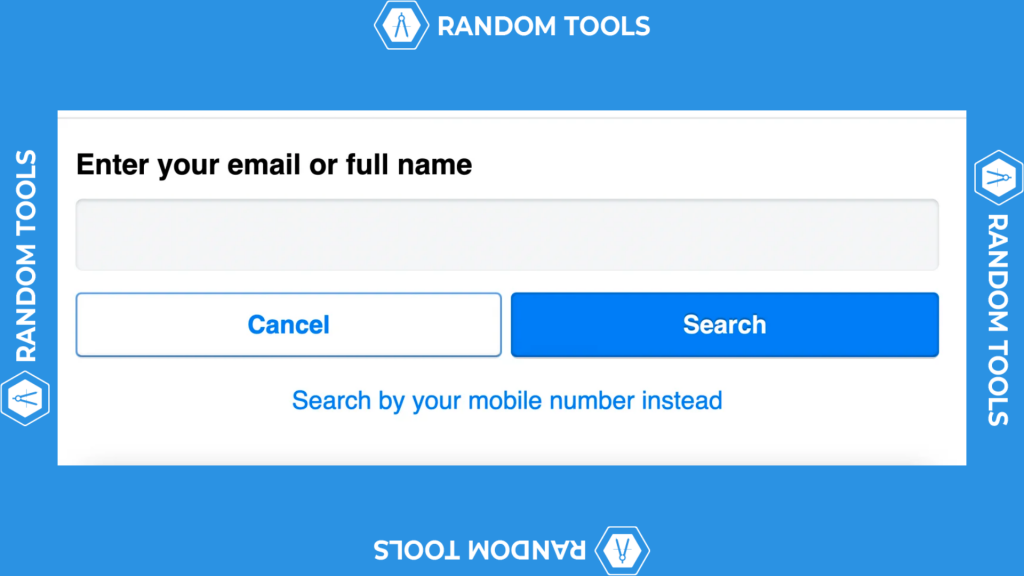 How to Find My Facebook Account by My Name05 julho 2024
How to Find My Facebook Account by My Name05 julho 2024 -
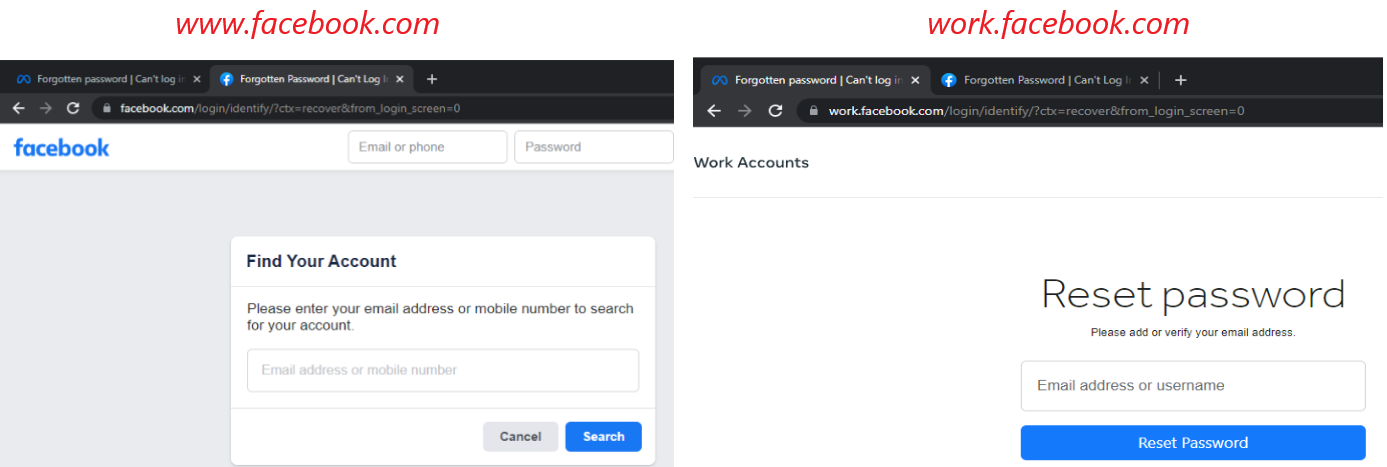 Contact Point Deanonymization Vulnerability in Meta05 julho 2024
Contact Point Deanonymization Vulnerability in Meta05 julho 2024 -
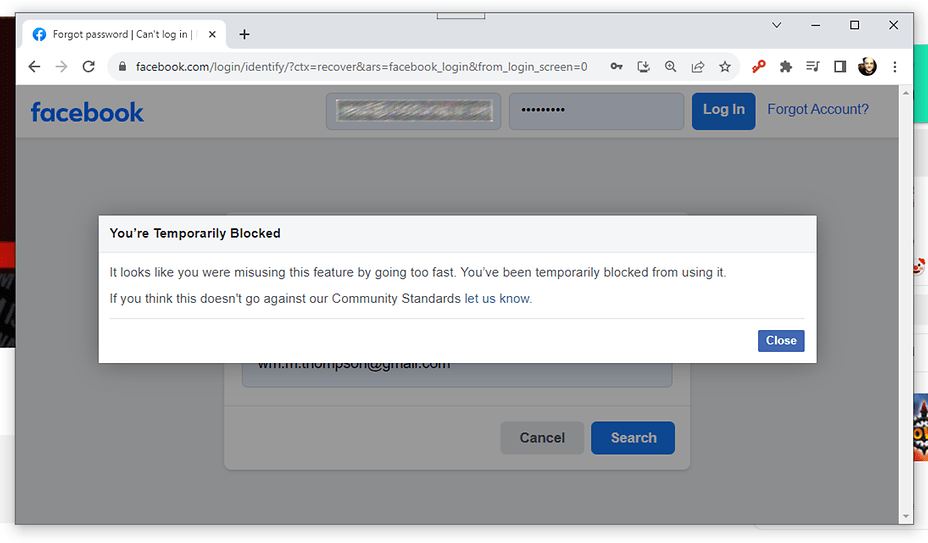 Using Facebook05 julho 2024
Using Facebook05 julho 2024 -
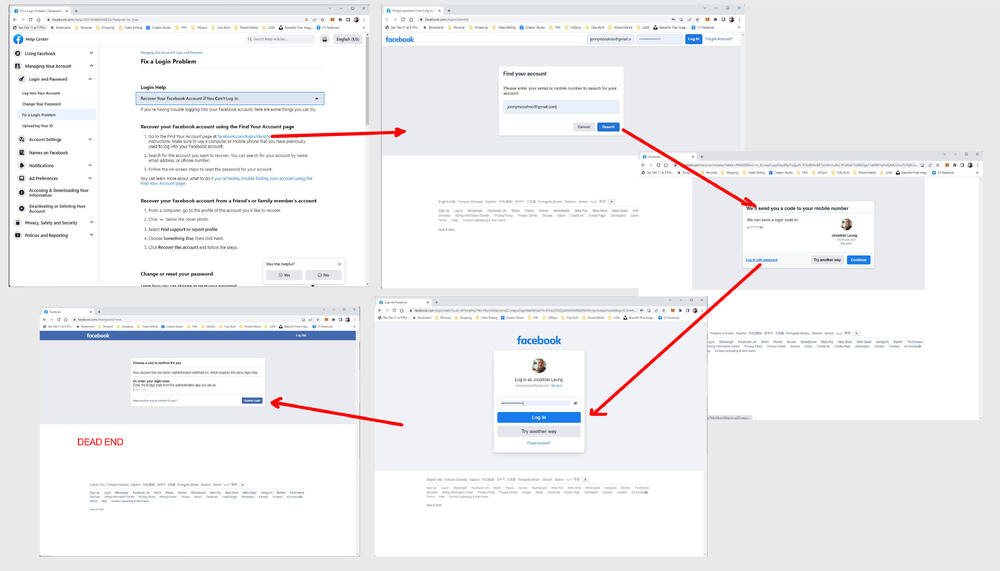 Big Corporation VS Small Business - Facebook's 2FA Nightmare Loop05 julho 2024
Big Corporation VS Small Business - Facebook's 2FA Nightmare Loop05 julho 2024 -
 How am i even supposed to confirm it when everything is logged out05 julho 2024
How am i even supposed to confirm it when everything is logged out05 julho 2024
você pode gostar
-
 STALKER 2: Heart of Chernobyl receives its first gameplay trailer05 julho 2024
STALKER 2: Heart of Chernobyl receives its first gameplay trailer05 julho 2024 -
 Motorola Moto G Power 5G 2023 256GB (Unlocked) Mineral Black PAWA0003US - Best Buy05 julho 2024
Motorola Moto G Power 5G 2023 256GB (Unlocked) Mineral Black PAWA0003US - Best Buy05 julho 2024 -
 A Plague Tale: Requiem now has a 60fps option - so what's the05 julho 2024
A Plague Tale: Requiem now has a 60fps option - so what's the05 julho 2024 -
 Pokemon Fire Red Randomizer Nuzlocke Ep21 Its Done!05 julho 2024
Pokemon Fire Red Randomizer Nuzlocke Ep21 Its Done!05 julho 2024 -
 Foxy 167: A Secret Weapon in the Exchange Ruy Lopez - Chess Opening Video DVD05 julho 2024
Foxy 167: A Secret Weapon in the Exchange Ruy Lopez - Chess Opening Video DVD05 julho 2024 -
 FIFA World Cup 2022 Soccer Jersey Patch Qatar FIFA Football Patch05 julho 2024
FIFA World Cup 2022 Soccer Jersey Patch Qatar FIFA Football Patch05 julho 2024 -
 Half-Life Alyx guide: One essential tip for dealing with Jeff – Destructoid05 julho 2024
Half-Life Alyx guide: One essential tip for dealing with Jeff – Destructoid05 julho 2024 -
 Retrospectiva: 15 memes mais engraçados de 2020!05 julho 2024
Retrospectiva: 15 memes mais engraçados de 2020!05 julho 2024 -
 9+ Thousand Casino Gift Royalty-Free Images, Stock Photos & Pictures05 julho 2024
9+ Thousand Casino Gift Royalty-Free Images, Stock Photos & Pictures05 julho 2024 -
Andrea Botez on X: I made a Fanhouse! Lately I've been traveling a lot, and I'd like to share more casual content behind the scenes and random moments from my life 🙂05 julho 2024
